What are click bots and how can I stop them?
Adwords clicker bots have driven PPC marketers demented for as long as paid digital marketing has been around. These click for cash robots won’t stop at anything to diminish your marketing budget and over the past few years, many have become quite sophisticated.
According to a study by the University of Baltimore, PPC marketing managers face a $23.7 billion click-fraud loss in 2020 alone.
In this post let’s take a look at some of the most famous click bots and ad fraud malware campaigns, and how they’ve progressed over the years.
And most importantly, find out what you can do to avoid falling prey to websites where click bots are hiding and selling their ‘soul’ to the highest bidder.
What is a click bot?
These automated ad clickers are pieces of code that are designed to click on whatever the fraudster wants them to i.e your Google Ad placements.
In the case of PPC fraud, the focus is on PPC ads (Google Display Network ads, YouTube display ads, or responsive text ads), which are normally embedded on a website owned by a fraudster.
The idea is that the fraudster then collects cash payouts for the clicks (or video impressions) on the ads that his site is hosting. And meanwhile, your ad account is paying for wasted views.
The bots themselves are in essence a type of virus, or Trojan, most often embedded on a desktop, tablet, server or cellphone.
Once embedded on a device, they can then be used as part of a network to click on multiple ads, multiple times. Or they can also carry out localised click fraud, for example within an app, click injection or click spamming.
Whatever the tactic, every ad click costs a business money.
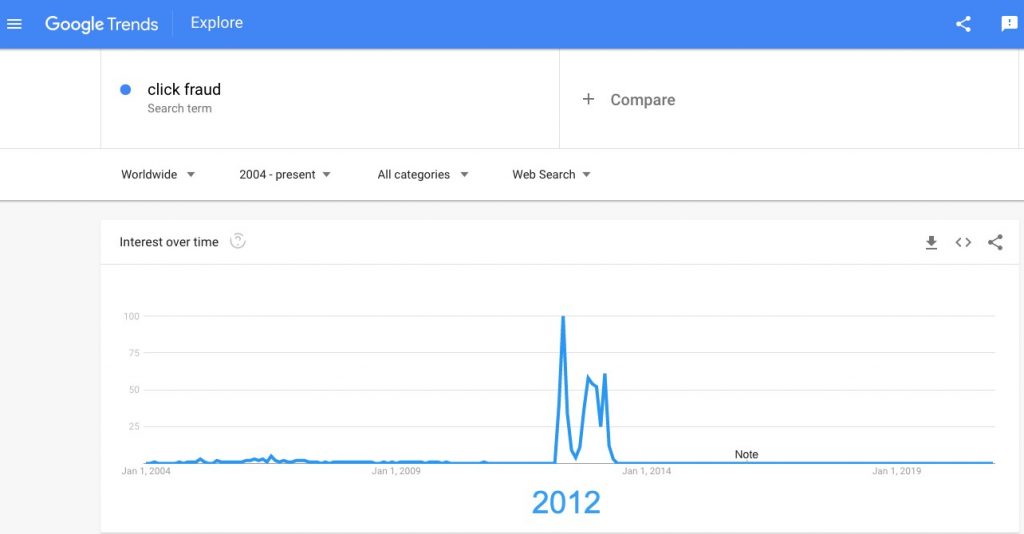
Since the early 2000s, Google users have known about click fraud, with a peak in interest in 2012, the year that Facebook was brought to court by RootZoo. But when did click fraud, or ad fraud, start to become the huge problem that it is today?
History of click fraud
Mentions of click fraud before 2006 related to the practice of fraudsters hosting ads on low-quality websites and then clicking them to collect the payout.
This was a simple manoeuvre, with fraudulent publishers signing up their scam site on Google AdSense and then clicking the ads themselves (or hiring someone to do it for them).
Even as far back as 2003, there were mentions of bots but much of the information was based on assumptions.
And so, knowing there was a problem with click fraud, Google employed a dedicated team to address the fast-growing problem.
Competitor click fraud has also been a problem since the early days of pay-per-click, with the practice becoming commonplace today, especially in competitive markets.
Clickbot A
In 2006, Google identified malicious software that was used to conduct low-noise click fraud attacks against the Google Display Network.
In essence, Clickbot A had its sights set on search results on sites that used Google to provide the sponsored results. It was thought that around 100,000 machines powered this Adwords clicker bot.
As the first known mention of an actual ad clicker, Clickbot A is the first evidence we have for the existence of click fraud botnets.
Google estimated that Clickbot A was responsible for $50,000 worth of fraud. A drop in the ocean for what today’s criminal enterprises can collect. And, as we’ll see, this is nothing compared to those that would follow in Clickbot A’s footsteps.
DNSChanger

Created by a team of Estonians and Russians known as Rove Digital, the DNSChanger scam is probably one of the first known court cases against an ad fraud network.
Vladimir Tsastin was sentenced and convicted on charges of wire fraud and money laundering and went to jail for seven years having pocketed over $14 million.
This botnet worked by infecting Microsoft Internet Explorer and then changing the web address of the infected devices to domains owned by the gang. The browser would then display ads which would earn a commission for the Rove Digital fraudsters.
The DNSChanger botnet ran for around 4 years and, as well as click bots, there were features such as preventing anti-virus updates, which helped it evade detection for so long.
Miuref
Also known as Boaxxe, was more than just a click bot. As a Trojan, it was often delivered via email attachments such as fake documents and was used in a variety of online fraud attacks.
Most famously, Miuref was used to devastating effect as part of the 3ve botnet campaign. But it can also be used to remotely mine Bitcoin, steal data, and take advantage of security vulnerabilities.
Although it has been identified and can be removed by antivirus software, Miuref continues to be a problem and still wreaks havoc where it can.
It’s unclear exactly how much financial damage Miuref caused, as it is often used with other botnets. And, as it isn’t specifically an ad fraud bot clicker, it’s financial impact is estimated to be in the multi-billions.
Methbot
The granddaddy of click fraud botnets, Methbot used a network of infected servers to trick websites and perform fake video ad impressions. It’s thought that the gang behind Methbot were making up to $5 million a day in fake ad impressions.
Although, as we’ve seen, ad fraud is nothing new, the unique feature of Methbot was its ability to make fake inventory look like genuine premium inventory.
The sheer volume of fraud being committed by Methbot made headlines and struck fear into the heart of the digital advertising world.
Today, it’s still the benchmark for click fraud campaigns. Although, it’s cousin, 3ve, was soon to replace Methbot as the biggest fraud network.
3ve (pronounced Eve)
Just as Methbot was being shut down by the FBI, a new and improved ad fraud network came into existence. 3ve was run by most of the same team behind Methbot, but the complexity of this ad fraud scheme took click bots to another level.
By using click fraud bots such as Kovter and Miuref, 3ve was capable of spoofing even more video impressions. In addition, 3ve managed to work despite the ads.txt – actually using ads.txt lists to spoof inventory.
It turned out that a team of Russian and Kazakh nationals were behind this huge scam, making an estimated $29 million with their scheme.
Tekya
This ad clicker or klick bots as they say in Germany was hidden in at least 56 Android apps, mostly kids games but with a few utilities apps in there too. The Tekya malware would engage with ads without the knowledge of the user.
With over 1 million downloads, it’s thought that Tekya had committed ad fraud since May 2019. Tekya used a clicker malware called Haken, which mimics user behavior and clicks on both visible and invisible ads on a device screen.
This was an intimidatingly sophisticated new addition to the world of criminal click fraud.
Does Google remove invalid clicks?
Due to the gargantuan size of the Google Display Network, Google can’t remove every click fraud website, and once they do more will just appear.
However, there are ways to take matters into your own hands to prevent click fraud from eating away at your Google Ads budget.
How can I protect my ad campaigns from PPC bots?
Click fraud is costly and there is no way to avoid it with 100% certainty.
Nevertheless, you can reduce your exposure by doing the following.
- Set up IP exclusions in Google Ads
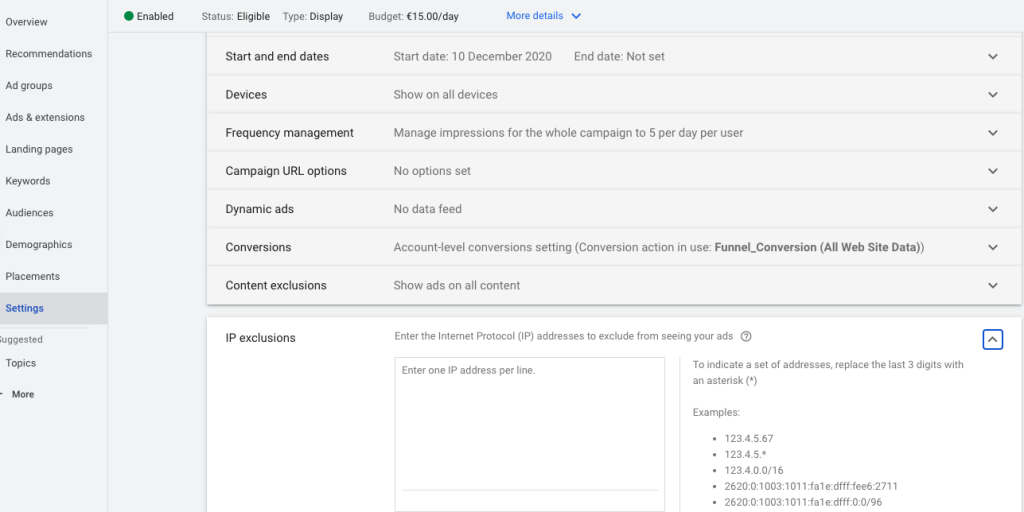
If you’ve done your analysis correctly and found that there are certain IP addresses responsible for click fraud, you can block your Google Ad placements from being served to those IP addresses in the future.
You simply need to set up an exclusion in your Google Ads account. Click on the settings, then additional settings.
Scroll down to the very bottom of the page and click IP exclusions.
Type in the offending addresses, (up to 500 per campaign).
Unfortunately, you can only add one per line, so if you paste a list of IP addresses you will need to sort them after.
That’s it!
For all other campaigns, Google will not display your ads to these IP addresses.
This is an effective way to protect your account from click fraudsters. However, the bad news is it can be incredibly time-consuming.
NB: Be sure not to exclude potential customers.
Users often have multiple IP addresses because they browse the internet at home, work, and in cafes.
This doesn’t mean that they should be added to your list. Make sure that you have done your homework before excluding them.
- Adjust your ad targeting
A small adjustment to your ad targeting could be all that’s needed to reduce fraudulent clicks. Is your click fraud coming from a specific geographic region or country?
They are not always located in the same place, but typically they will be in less developed nations.
Exclude these locations and their language from your Google Ads campaigns. If you suspect that your main competitor is the culprit, exclude their postcode.
NB: Be careful not to block high converting traffic when excluding locations.
- Use Google remarketing campaigns
Google Ads remarketing is a form of digital advertising that lets businesses show targeted ads to people who have already visited their website.
Past visitors will see these ads while they are browsing the web, watching YouTube videos or reading news sites, for example.
Thus, keeping your brand top-of-mind and enticing visitors to return to your page. Maybe they visited certain web pages, downloaded a free guide, or put something in a shopping cart, etc.
There’s no risk of click fraudsters accessing these ads because they can’t see them.
- Create a placement exclusion list(s)

All ad agencies will have an extensive placement exclusion list.
Make sure to inquire about how often they update their list, as ideally, you need to do this daily because it’s a work in progress.
When you complete an ad campaign you will find out if certain websites are poor performing.
We recommend that every business has a vertical-specific placement exclusion list that they update regularly.
If you don’t have time, the team at AdShield has created software that combs millions of websites for the latest post-click performance and it uploads this Google placement exclusion list directly to your Google ads account. It works by
- Analyzing billions of placements and click-behavior.
- Combining placement data with data on user behavior on the landing page of the advertiser, focusing on conversions/events.
- Automatically pre-blocking low-quality websites and apps from your Google ad campaigns.
- Directly uploading to your Google ad account.
The software reveals placement performance for a vast array of advertisers and URLs.
AdShield also maintains vertical-specific exclusion lists. These lists are updated daily, with new poor performing placements added to different placement exclusion lists.
There are currently 450k exclusions on our list.